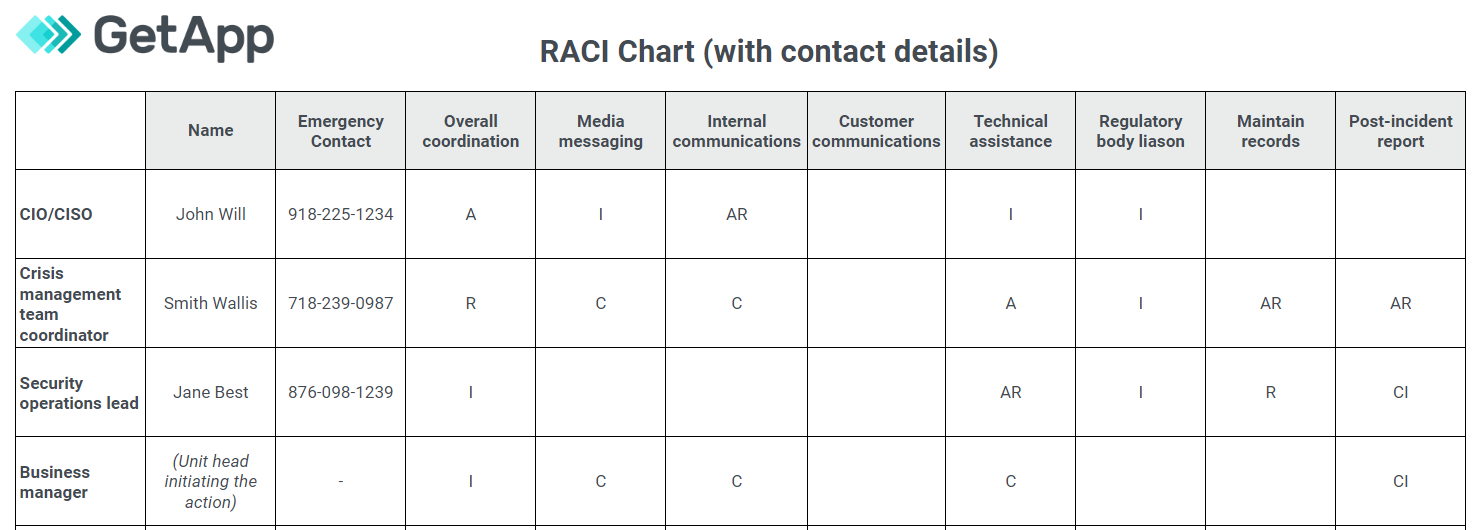
Cybersecurity Plan Template
Cybersecurity plan template - Plan for the response when a compromise occurs; Use of this checklist does not create a safe harbor. Using these steps, your organization can create a leadership development plan template to follow. This checklist is primarily derived from the national institute of standards and technology (nist) cybersecurity framework and finra’s report on cybersecurity practices. 2020 information security plan template instructions. Establishing iot device cybersecurity requirements. Find information about it planning, cybersecurity, and data management for your organization. Iot device cybersecurity guidance for the federal government: Implement a plan to recover lost, stolen or unavailable assets. Emotional intelligence in the workplace;
A comprehensive investigation plan should be created before beginning a new investigation. It’s the best way to ensure the investigation stays on track and keeps everyone accountable and following a logical process. Establishing iot device cybersecurity requirements. Cui plan of action template. Use this detailed investigation plan template to ensure your next investigation starts off on the right foot.
Cybersecurity Guidance for Small Firms Cybersecurity Guidance for
Use of this checklist does not create a safe harbor. Using these steps, your organization can create a leadership development plan template to follow. Emotional intelligence in the workplace;
40 Cyber Incident Response Plan Template in 2020 (With images) How to
This checklist is primarily derived from the national institute of standards and technology (nist) cybersecurity framework and finra’s report on cybersecurity practices. In doing so, a culture of leadership and positive development will be established, and. Using these steps, your organization can create a leadership development plan template to follow.
How to Create a Cybersecurity Crisis Management Plan in 5 Steps
Using these steps, your organization can create a leadership development plan template to follow. Cui plan of action template. Find information about it planning, cybersecurity, and data management for your organization.
Nist 800 171 Template shatterlion.info
Use of this checklist does not create a safe harbor. Planning statewide technology priorities and reporting on progress. In doing so, a culture of leadership and positive development will be established, and.
Cyber Security Themed Deck for PowerPoint SlideModel
Planning statewide technology priorities and reporting on progress. Iot device cybersecurity guidance for the federal government: This checklist is primarily derived from the national institute of standards and technology (nist) cybersecurity framework and finra’s report on cybersecurity practices.
Cyber Security Proposal Template Project manager resume, Engineering
A comprehensive investigation plan should be created before beginning a new investigation. Establishing iot device cybersecurity requirements. Find information about it planning, cybersecurity, and data management for your organization.
Computer Systems Digital Assets PowerPoint Diagram SlideModel
Using these steps, your organization can create a leadership development plan template to follow. A comprehensive investigation plan should be created before beginning a new investigation. Use of this checklist does not create a safe harbor.
Service Level Requirements Template Example
Using these steps, your organization can create a leadership development plan template to follow. Implement a plan to recover lost, stolen or unavailable assets. A comprehensive investigation plan should be created before beginning a new investigation.
Using these steps, your organization can create a leadership development plan template to follow. This checklist is primarily derived from the national institute of standards and technology (nist) cybersecurity framework and finra’s report on cybersecurity practices. Iot device cybersecurity guidance for the federal government: Find information about it planning, cybersecurity, and data management for your organization. Use this detailed investigation plan template to ensure your next investigation starts off on the right foot. 2020 information security plan template instructions. It’s the best way to ensure the investigation stays on track and keeps everyone accountable and following a logical process. Cui plan of action template. A comprehensive investigation plan should be created before beginning a new investigation. Implement a plan to recover lost, stolen or unavailable assets.
Establishing iot device cybersecurity requirements. Emotional intelligence in the workplace; Planning statewide technology priorities and reporting on progress. In doing so, a culture of leadership and positive development will be established, and. Use of this checklist does not create a safe harbor. Plan for the response when a compromise occurs; Establishing iot device cybersecurity requirements.