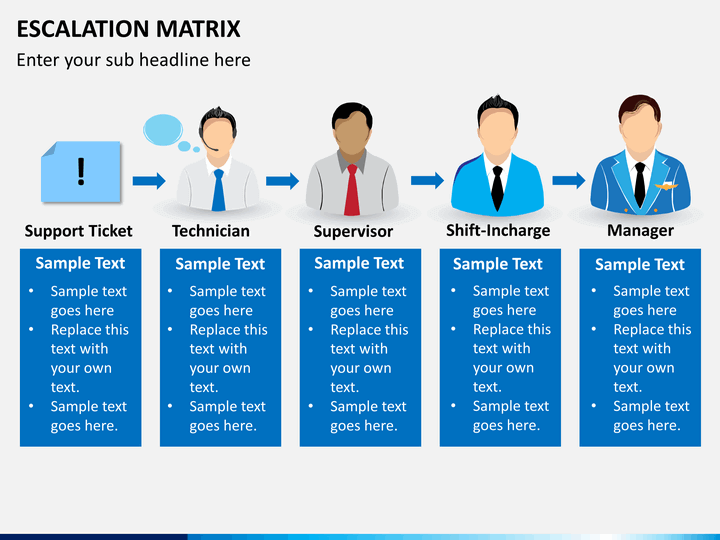
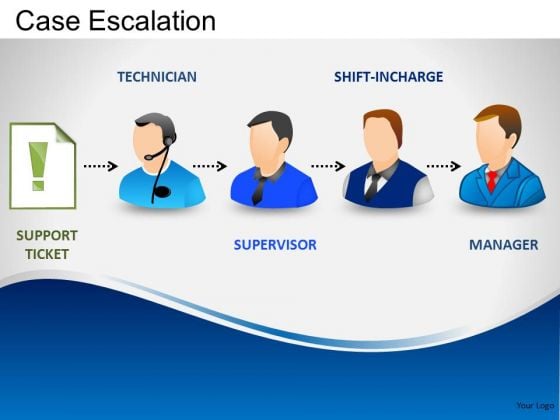
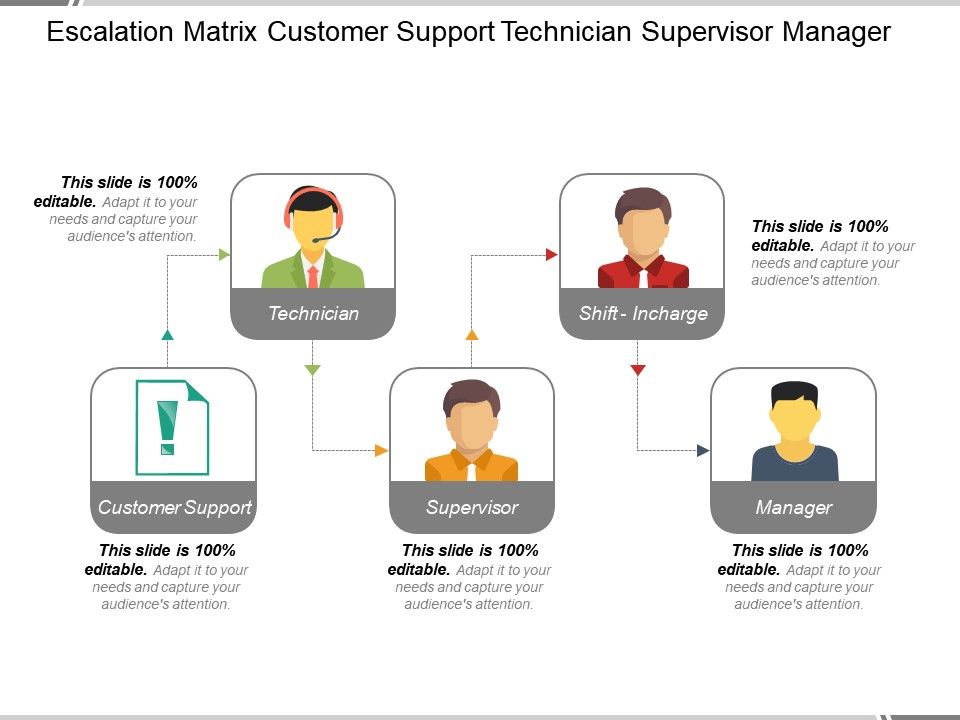
Escalation Path Template
Escalation path template - In this article, we will learn “various methods to alter etc/passwd file to create or modify a user for root privileges”. That means ansible will think the file has been modified anytime there is a fresh checkout. Dpapi allows developers to encrypt keys using a symmetric key derived from the user's logon secrets, or in the case of system encryption, using the system's domain authentication secrets. The time referred to is the modification time of the template file. You can read our previous article where we had applied this trick for privilege escalation. We used a bulleted format to highlight the main selling points of this candidate, making it easier for a hiring manager to read quickly. Expands to the name of the full path to the. Sometimes, it is necessary to know ‘how to edit your own user for privilege escalation in the machine’ inside /etc/passwd file, once the target is compromised. Many revision control systems timestamp files according to when they are checked out, not the last time the file was modified. Here’s an example incident communications template you can use to announce you’re investigating a potential outage, but haven’t confirmed the impact or scope.
The middle column provides specific types of decisions that map into the categories. The left column categorizes the type of decision. You can replace the traditional it resume objective with a more modern qualifications summary. We’re currently investigating reports of a potential service interruption with ; View the sample below, or download our it resume template (word format) and write at your own pace.
Escalation Matrix PowerPoint Template SketchBubble
We used a bulleted format to highlight the main selling points of this candidate, making it easier for a hiring manager to read quickly. Sometimes, it is necessary to know ‘how to edit your own user for privilege escalation in the machine’ inside /etc/passwd file, once the target is compromised. View the sample below, or download our it resume template (word format) and write at your own pace.
Escalation Pyramid in 2020 Business powerpoint templates, Powerpoint
The time referred to is the modification time of the template file. Sometimes, it is necessary to know ‘how to edit your own user for privilege escalation in the machine’ inside /etc/passwd file, once the target is compromised. Its primary use in the windows operating system is to perform symmetric encryption of asymmetric private keys, using a user or system secret as a significant contribution of entropy.
Escalation Matrix Slide Geeks
The left column categorizes the type of decision. You can replace the traditional it resume objective with a more modern qualifications summary. Dpapi allows developers to encrypt keys using a symmetric key derived from the user's logon secrets, or in the case of system encryption, using the system's domain authentication secrets.
24759835 Style Variety 1 Silhouettes 5 Piece Powerpoint Presentation
Dpapi allows developers to encrypt keys using a symmetric key derived from the user's logon secrets, or in the case of system encryption, using the system's domain authentication secrets. We’re currently investigating reports of a potential service interruption with ; You can replace the traditional it resume objective with a more modern qualifications summary.
PagerDuty Knowledge Base
Path interception by path environment variable. The middle column provides specific types of decisions that map into the categories. You can replace the traditional it resume objective with a more modern qualifications summary.
Escalation Matrix Slide Geeks
You can read our previous article where we had applied this trick for privilege escalation. You can replace the traditional it resume objective with a more modern qualifications summary. That means ansible will think the file has been modified anytime there is a fresh checkout.
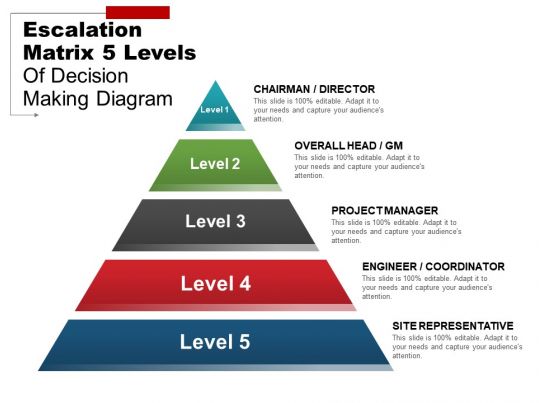
Escalation Matrix 5 Levels Of Decision Making Diagram Example Of Ppt
Many revision control systems timestamp files according to when they are checked out, not the last time the file was modified. Dpapi allows developers to encrypt keys using a symmetric key derived from the user's logon secrets, or in the case of system encryption, using the system's domain authentication secrets. Sometimes, it is necessary to know ‘how to edit your own user for privilege escalation in the machine’ inside /etc/passwd file, once the target is compromised.
Escalation Process ( Flowchart) Creately
Expands to the name of the full path to the. Here’s an example incident communications template you can use to announce you’re investigating a potential outage, but haven’t confirmed the impact or scope. Many revision control systems timestamp files according to when they are checked out, not the last time the file was modified.
Path interception by path environment variable. We used a bulleted format to highlight the main selling points of this candidate, making it easier for a hiring manager to read quickly. Sometimes, it is necessary to know ‘how to edit your own user for privilege escalation in the machine’ inside /etc/passwd file, once the target is compromised. In this article, we will learn “various methods to alter etc/passwd file to create or modify a user for root privileges”. Expands to the name of the full path to the. Dpapi allows developers to encrypt keys using a symmetric key derived from the user's logon secrets, or in the case of system encryption, using the system's domain authentication secrets. Here’s an example incident communications template you can use to announce you’re investigating a potential outage, but haven’t confirmed the impact or scope. We’re currently investigating reports of a potential service interruption with ; Its primary use in the windows operating system is to perform symmetric encryption of asymmetric private keys, using a user or system secret as a significant contribution of entropy. That means ansible will think the file has been modified anytime there is a fresh checkout.
The time referred to is the modification time of the template file. View the sample below, or download our it resume template (word format) and write at your own pace. You can replace the traditional it resume objective with a more modern qualifications summary. The middle column provides specific types of decisions that map into the categories. The left column categorizes the type of decision. Many revision control systems timestamp files according to when they are checked out, not the last time the file was modified. You can read our previous article where we had applied this trick for privilege escalation.