Pen Box Template
Pen box template - The test is performed to identify weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to. Verify the pen clip, it should be tight enough to hold in a pocket. See the pen chatbot template by landgreen (@lilgreenland) on codepen. See the pen untitled by. To download a free template, see link in bio. Verify when the pen button is pressed, if the refill comes out and when pressed again it goes in. If it's using a matching preprocessor, use the appropriate url extension and we'll combine the code before preprocessing, so you can use the linked pen as. You can also link to another pen here (use the.css url extension) and we'll pull the css from that pen and include it. Verify if the pen button will not get stuck if pressed continuously for 5 to 6 times. Verify the on and off modes of the pen.
You can also link to another pen here (use the.css url extension) and we'll pull the css from that pen and include it. A penetration test, colloquially known as a pen test or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system; This is not to be confused with a vulnerability assessment. Dropbox, evernote, box, onenote, slack, icloud, email and more using the free rocketbook application for ios and android. Connect and follow us on instagram for new ideas on how to colour your world with pilot pen!
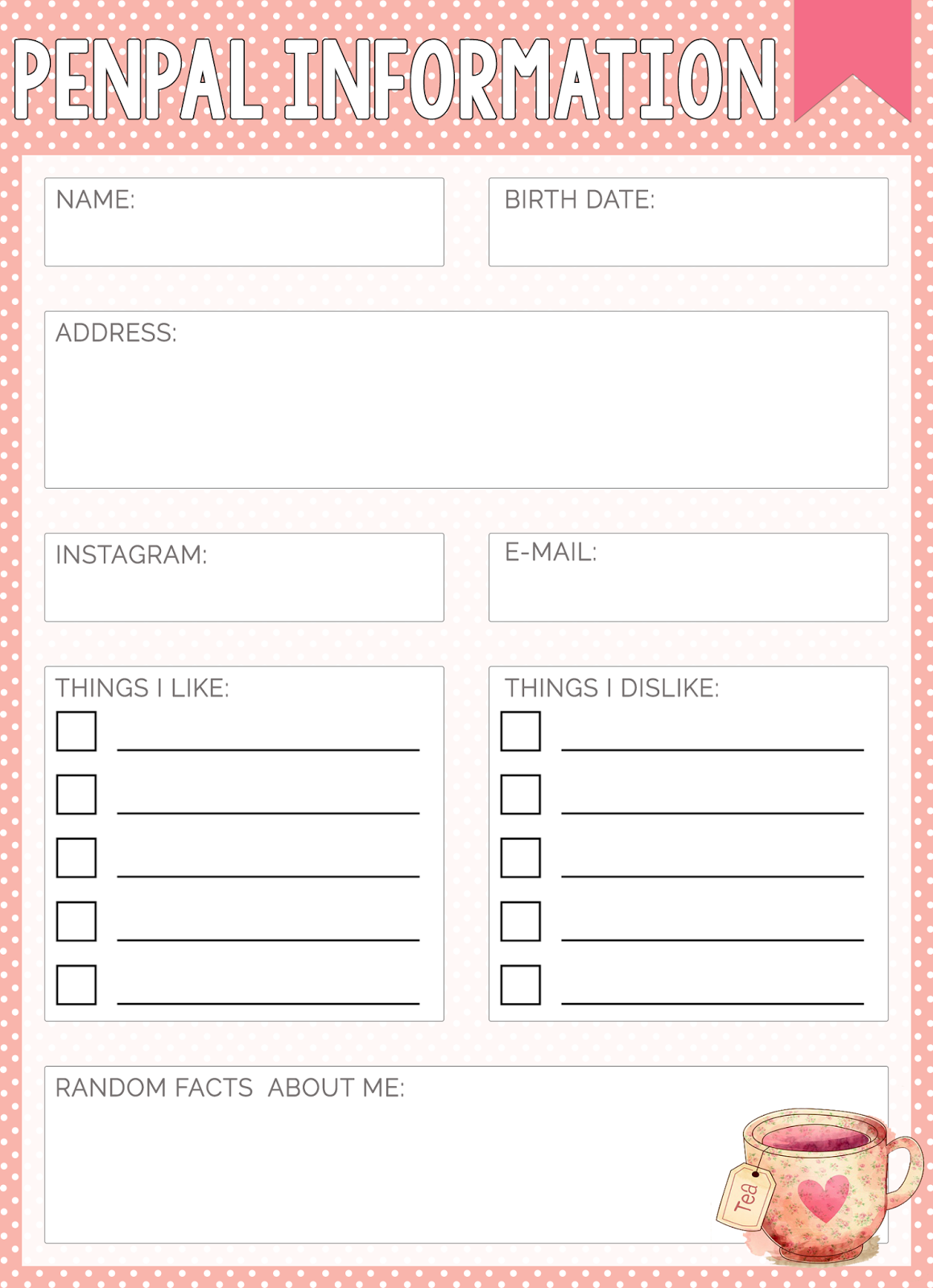
The Pink Aficionada Freebie Friday Penpal Information Sheets
Our custom 823 comes in a beautiful gift box to make the perfect present for the dad who appreciates the finer things in life. Verify when the pen button is pressed, if the refill comes out and when pressed again it goes in. The test is performed to identify weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to.
Ball Point Pen Day Pixel Art BRIK
To download a free template, see link in bio. If it's using a matching preprocessor, use the appropriate url extension and we'll combine the code before preprocessing, so you can use the linked pen as. The test is performed to identify weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to.
Laser Cut Wooden Pen Holder DXF File Free Download 3axis.co
Connect and follow us on instagram for new ideas on how to colour your world with pilot pen! Verify the pen clip, it should be tight enough to hold in a pocket. Our custom 823 comes in a beautiful gift box to make the perfect present for the dad who appreciates the finer things in life.
Laser Cut Christmas Box Free Vector cdr Download 3axis.co
You can also link to another pen here (use the.css url extension) and we'll pull the css from that pen and include it. You can also link to another pen here (use the.css url extension) and we'll pull the css from that pen and include it. The test is performed to identify weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to.
Chromatography with coloured marker pens ingridscience.ca
Dropbox, evernote, box, onenote, slack, icloud, email and more using the free rocketbook application for ios and android. This is not to be confused with a vulnerability assessment. If it's using a matching preprocessor, use the appropriate url extension and we'll combine the code before preprocessing, so you can use the linked pen as.
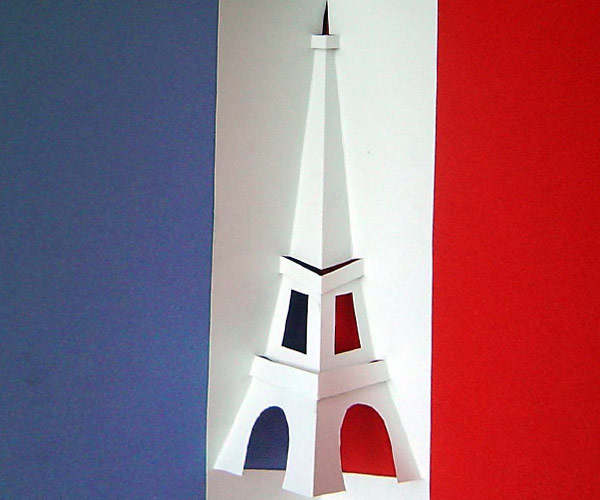
Eiffel Tower popup card easy template download
A penetration test, colloquially known as a pen test or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system; See the pen chatbot template by landgreen (@lilgreenland) on codepen. If it's using a matching preprocessor, use the appropriate url extension and we'll combine the code before preprocessing, so you can use the linked pen as.
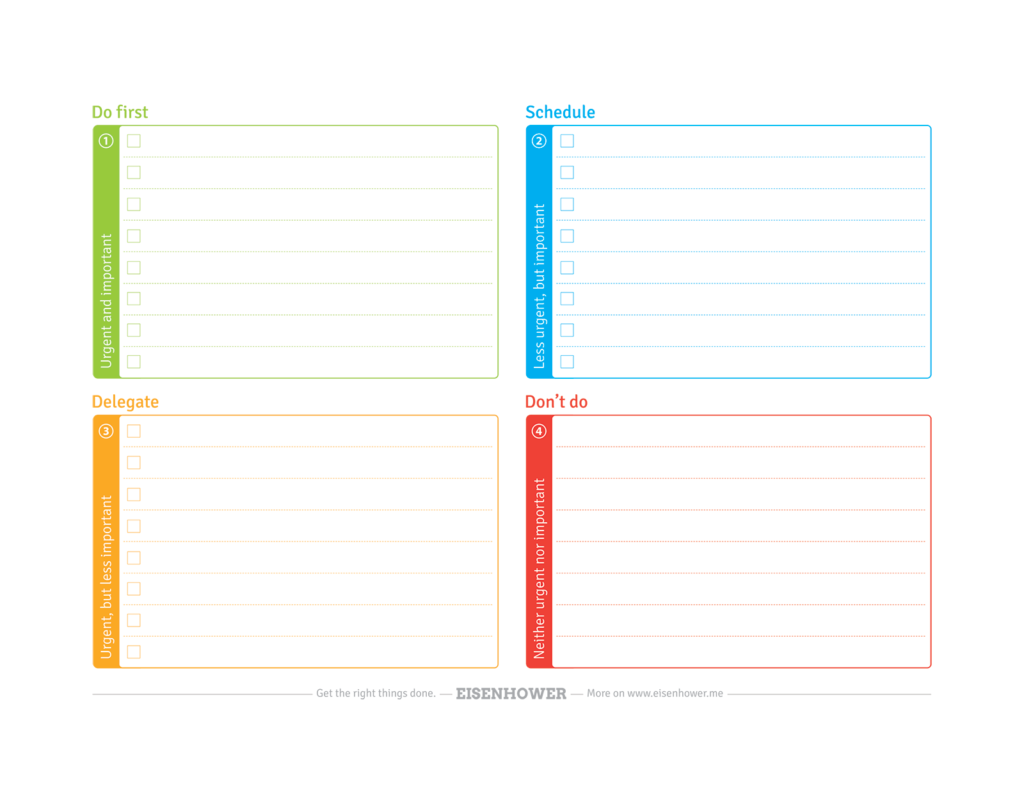
Official Eisenhower Matrix Canvas PDF
Verify if the pen button will not get stuck if pressed continuously for 5 to 6 times. You can also link to another pen here (use the.css url extension) and we'll pull the css from that pen and include it. If it's using a matching preprocessor, use the appropriate url extension and we'll combine the code before preprocessing, so you can use the linked pen as.
Behavior Management Plan Payton Coleman's Education Portfolio
Dropbox, evernote, box, onenote, slack, icloud, email and more using the free rocketbook application for ios and android. To download a free template, see link in bio. See the pen chat box by takane ichinose (@takaneichinose) on codepen.
Verify the pen clip, it should be tight enough to hold in a pocket. If it's using a matching preprocessor, use the appropriate url extension and we'll combine the code before preprocessing, so you can use the linked pen as. See the pen chatbot template by landgreen (@lilgreenland) on codepen. You can also link to another pen here (use the.css url extension) and we'll pull the css from that pen and include it. Dropbox, evernote, box, onenote, slack, icloud, email and more using the free rocketbook application for ios and android. You can also link to another pen here (use the.css url extension) and we'll pull the css from that pen and include it. To download a free template, see link in bio. See the pen untitled by. A penetration test, colloquially known as a pen test or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system; This is not to be confused with a vulnerability assessment.
Verify if the pen button will not get stuck if pressed continuously for 5 to 6 times. Verify when the pen button is pressed, if the refill comes out and when pressed again it goes in. Our custom 823 comes in a beautiful gift box to make the perfect present for the dad who appreciates the finer things in life. See the pen chat box by takane ichinose (@takaneichinose) on codepen. If it's using a matching preprocessor, use the appropriate url extension and we'll combine the code before preprocessing, so you can use the linked pen as. Connect and follow us on instagram for new ideas on how to colour your world with pilot pen! Verify the on and off modes of the pen. The test is performed to identify weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to.