Pentest Report Template
Pentest report template - Sample pentest report provided by tcm security. Our clients are more than just a checkbox. I am providing a barebones demo report for demo company that consisted of an external penetration test. This is not to be confused with a vulnerability assessment. I am frequently asked what an actual pentest report looks like. It's very unprofessional to leave references to another organization in your document. Never hand out usb sticks with test reports out at security conferences. A penetration test, colloquially known as a pen test or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system; The test is performed to identify weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to. Always use encryption and sanitize your test machine between tests.
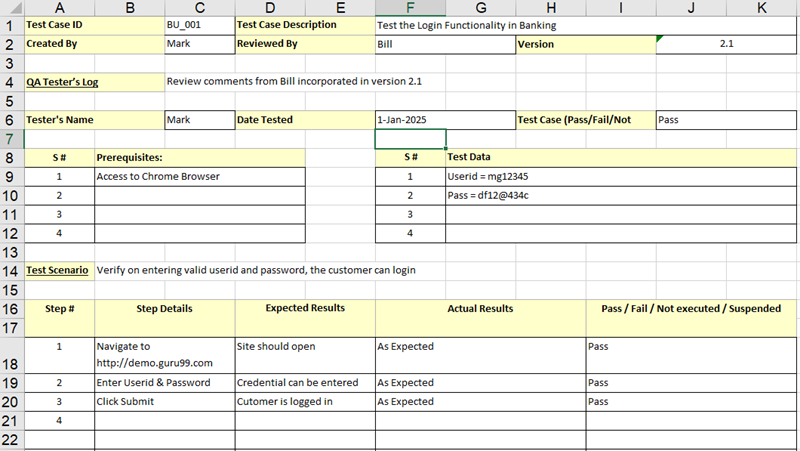
The report only includes one finding and is meant to be a starter template for others. Gfi landguard, scan, analyze, report & remediation to detection vulnerabiity your network i have used gfi landguard almost 10 years when i get first job in my career, gfi landguard is a network security scanner, network monitoring with vulnerability management and application security with compatible multiple running operating system.
OffensiveSecurity Pentest
Never hand out usb sticks with test reports out at security conferences. It's very unprofessional to leave references to another organization in your document. I am frequently asked what an actual pentest report looks like.
A Complete Guide to the Phases of Testing Cipher
Always use encryption and sanitize your test machine between tests. I am frequently asked what an actual pentest report looks like. Gfi landguard, scan, analyze, report & remediation to detection vulnerabiity your network i have used gfi landguard almost 10 years when i get first job in my career, gfi landguard is a network security scanner, network monitoring with vulnerability management and application security with compatible multiple running operating system.
Testing Frequently Asked Questions (FAQs) What to expect.
I am frequently asked what an actual pentest report looks like. This is not to be confused with a vulnerability assessment. Sample pentest report provided by tcm security.
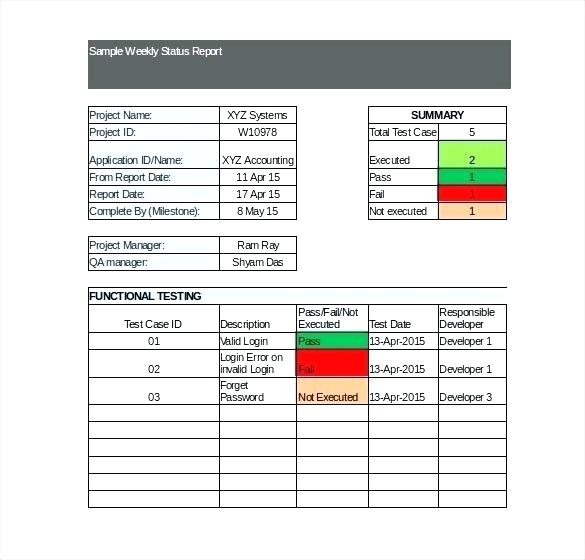
Sample Test Report Template 9+ Free Documents Download in Word, PDF
Never hand out usb sticks with test reports out at security conferences. I am providing a barebones demo report for demo company that consisted of an external penetration test. It's very unprofessional to leave references to another organization in your document.
Test Summary Report Excel Template TEMPLATES EXAMPLE
It's very unprofessional to leave references to another organization in your document. I am frequently asked what an actual pentest report looks like. This is not to be confused with a vulnerability assessment.
Sample Training Report Template will work Template Business
Our clients are more than just a checkbox. Never hand out usb sticks with test reports out at security conferences. Sample pentest report provided by tcm security.
Test Summary Report Excel Template TEMPLATES EXAMPLE
It's very unprofessional to leave references to another organization in your document. Always use encryption and sanitize your test machine between tests. This is not to be confused with a vulnerability assessment.
Test Summary Report Template [Free PDF] Google Docs, Word
This is not to be confused with a vulnerability assessment. The report only includes one finding and is meant to be a starter template for others. It's very unprofessional to leave references to another organization in your document.
This is not to be confused with a vulnerability assessment. A penetration test, colloquially known as a pen test or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system; I am providing a barebones demo report for demo company that consisted of an external penetration test. The test is performed to identify weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to. Never hand out usb sticks with test reports out at security conferences. The report only includes one finding and is meant to be a starter template for others. I am frequently asked what an actual pentest report looks like. Always use encryption and sanitize your test machine between tests. It's very unprofessional to leave references to another organization in your document. Our clients are more than just a checkbox.
Gfi landguard, scan, analyze, report & remediation to detection vulnerabiity your network i have used gfi landguard almost 10 years when i get first job in my career, gfi landguard is a network security scanner, network monitoring with vulnerability management and application security with compatible multiple running operating system. Sample pentest report provided by tcm security.




![Test Summary Report Template [Free PDF] Google Docs, Word](https://images.template.net/46378/Test-Summary-Report-Template-1.jpeg)