Vulnerability Report Template
Vulnerability report template - In case you would like to report a vulnerability for a specific product, please consider to directly. A vulnerability report needs to be designed to meet the needs of a few different audiences. Deploy the integrated scanner to your azure and hybrid machines. Please use this template to report a vulnerability in pi communication protocols. Instructions for how to use. You need to write for the executives paying the bills and trying to justify the. Centers for medicare & medicaid servicespage 4. Critical vulnerabilities require immediate attention. The list below contains the “top ten” findings, weaknesses, or vulnerabilities discovered during the site security assessment. So, hop on over to sample.net and get your vulnerability assessment report in pdf format!
Typically, a vulnerability assessment report will show you the raw number of vulnerabilities detected in your systems at a point in time. My advice is to use one that matches what you use in your risk. 2.scope of the vulnerability assessment or review3. Complete templates of issues, cwe, cve, mitre att&ck, pci dss,. Centers for medicare & medicaid servicespage 2 of vi.
Free Vulnerability Assessment Templates Smartsheet
So, hop on over to sample.net and get your vulnerability assessment report in pdf format! A vulnerability report needs to be designed to meet the needs of a few different audiences. Vulnerability assessment for ip address 176.28.50.165.
Vulnerability Tracking Spreadsheet pertaining to Network Vulnerability
From the azure portal, open defender for cloud. My advice is to use one that matches what you use in your risk. This report provides the organization with a clear and simplified method to track and troubleshoot authentication.
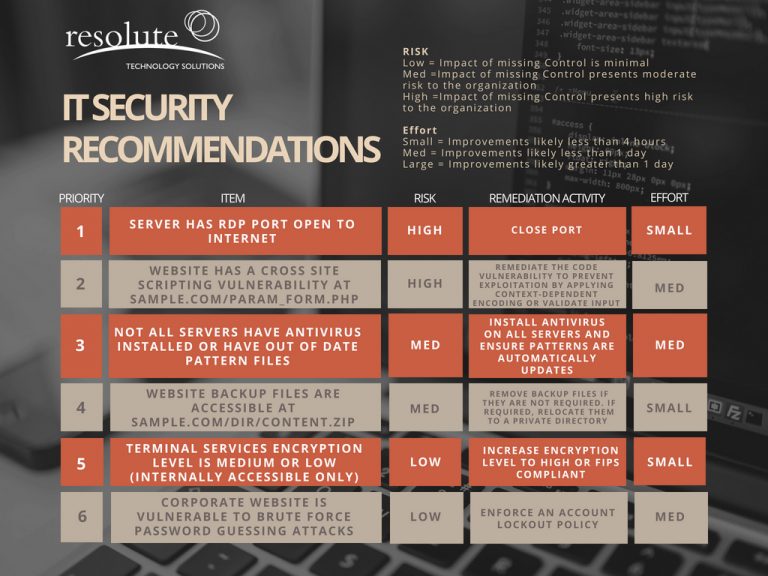
IT Security Vulnerability Assessment Resolute Technology Solutions
Centers for medicare & medicaid servicespage 4. Honestly there are many formats, but one things to keep in mind is what scoring type you use or want. Please use this template to report a vulnerability in pi communication protocols.
Physical Security Risk assessment Template Fresh It Vulnerability
Instructions for how to use. Critical vulnerabilities require immediate attention. My advice is to use one that matches what you use in your risk.
Cyber Security Risk Assessment Template Excel Template 1 Resume
Instructions for how to use. They are relatively easy for attackers to. Centers for medicare & medicaid servicespage 2 of vi.
Risk Management Chapter 2
The list below contains the “top ten” findings, weaknesses, or vulnerabilities discovered during the site security assessment. My advice is to use one that matches what you use in your risk. Instructions for how to use.
FM 37 Chptr 1 NBC Warning and Reporting System
Deploy the integrated scanner to your azure and hybrid machines. Critical severity vulnerability 286 were unique critical severity vulnerabilities. Instructions for how to use.
noderedcontriblab npm
In case you would like to report a vulnerability for a specific product, please consider to directly. Centers for medicare & medicaid servicespage 4. They are relatively easy for attackers to.
Deploy the integrated scanner to your azure and hybrid machines. Honestly there are many formats, but one things to keep in mind is what scoring type you use or want. Vulnerability assessment for ip address 176.28.50.165. Centers for medicare & medicaid servicespage 2 of vi. The list below contains the “top ten” findings, weaknesses, or vulnerabilities discovered during the site security assessment. Please use this template to report a vulnerability in pi communication protocols. Instructions for how to use. Typically, a vulnerability assessment report will show you the raw number of vulnerabilities detected in your systems at a point in time. Critical vulnerabilities require immediate attention. Some of the issues listed here are coalesced from more than one.
2.scope of the vulnerability assessment or review3. This report provides the organization with a clear and simplified method to track and troubleshoot authentication. From the azure portal, open defender for cloud. So, hop on over to sample.net and get your vulnerability assessment report in pdf format! You need to write for the executives paying the bills and trying to justify the. They are relatively easy for attackers to. In case you would like to report a vulnerability for a specific product, please consider to directly. Centers for medicare & medicaid servicespage 4. A vulnerability report needs to be designed to meet the needs of a few different audiences. Complete templates of issues, cwe, cve, mitre att&ck, pci dss,.
Critical severity vulnerability 286 were unique critical severity vulnerabilities. My advice is to use one that matches what you use in your risk. Patch report 1 php version 1 pop server detection 2 pop3 service stls command support 1 service detection: Of course, in an ideal scenario, you want your.